publications
publications by categories in reversed chronological order. generated by jekyll-scholar.
2026
-
USENIX Security26
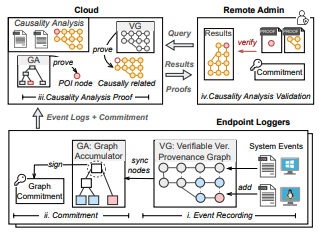 vCause: Efficient and Verifiable Causality Analysis for Cloud-based Endpoint AuditingIn the 35th USENIX Security 2026, 2026
vCause: Efficient and Verifiable Causality Analysis for Cloud-based Endpoint AuditingIn the 35th USENIX Security 2026, 2026 -
AAAI26
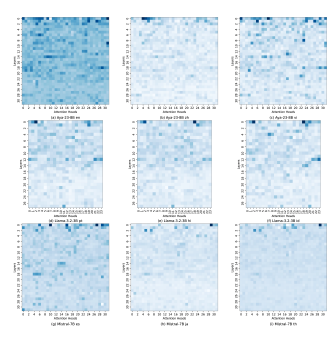 Focusing on Language: Revealing and Exploiting Language Attention Heads in Multilingual Large Language ModelsIn the 40th Association for the Advancement of Artificial Intelligence Conference (AAAI) 2026, 2026
Focusing on Language: Revealing and Exploiting Language Attention Heads in Multilingual Large Language ModelsIn the 40th Association for the Advancement of Artificial Intelligence Conference (AAAI) 2026, 2026